miho IT-Guidelines (Version: 21.04.2021)
Introduction
A successful remote access is the key to improved customer satisfaction due to lower cost and shorter shut-down times, it also safes resources on the side of the machine manufacturer.
Internet based technologies have been established as a standard, with the following advantages:
- Nearly the same worldwide coverage as the telephone network
- Universal, extendable and very failsafe network
- Only minimal danger of connection breaks
- Speed is scalable, usually only a question of the price
- Flexibility: The connection can be established via the existing customer network or a separate autarkic connection similar to a modem connection can be installed
However, the following disadvantages have to be considered:
- Security:
Information transported via the internet is using unsecured and sometimes anonymous connections as a matter of principle. Therefore the encryption of the transported data / information is mandatory.
Besides this, it must be avoided that unauthorized persons can obtain access to the customer’s machines. To achieve this, adequate means to identify the service engineer and also the customers machine, must be established - The network technology on which the internet is based requires a high level of specific knowledge to work with it
As far as security is concerned, one must understand that there is no such thing as 100% security, neither via the internet nor even without any external connection. If someone wants to obtain unauthorized access to a machine, there will be a way, even by using the weakest link on site, like bribing an employee. At the end it’s a question of the risk analysis and the adequate barriers which are installed to block a potential intruder.
As a summary we can state that the internet based remote access, especially for complex image processing systems is obligatory, if the proper security measures for this medium are implemented.
Technical Solution
The software suite OpenVPN is used for the encryption and authentication.
It has the following advantages:
- Authentication via state of the art „public key“ methods
- Modular, secure, encrypted transmission of data
- The complete communication is using only one port
- NAT-capability
- Easy to route through a network
- Several years of experience at miho, because it is used for our own in House remote access tasks
- Open source, no licence fees, no “vendor lock in”, fast and above all transparent remedy for security problems
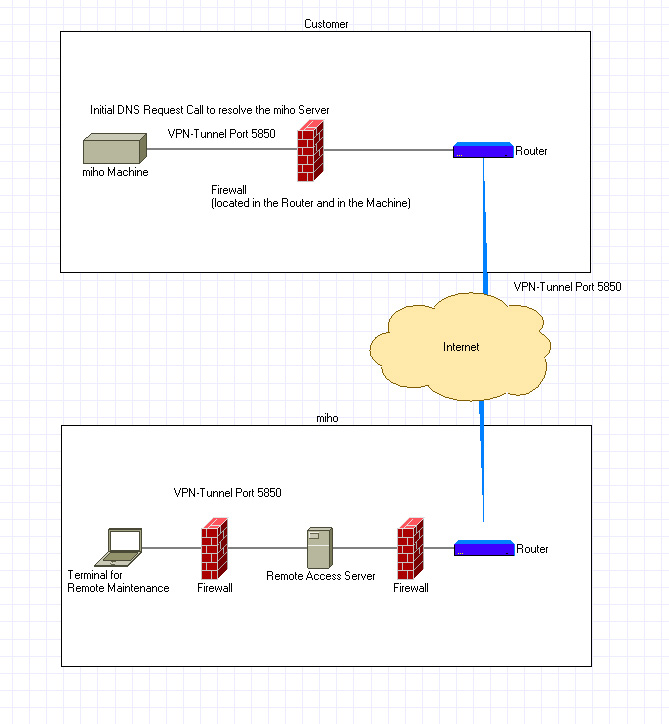
The technical side consists of a dedicated Remote Access server at miho (RA1) that is protected on both sides (towards the internet and miho) by firewalls.
If needed, the customer initiates a connection to this server via a VPN tunnel. From that moment onwards, a point to point connection between the customer’s machine and our Remote Access server exists. Each machine gets a unique certificate to identify itself at the miho Remote Access Server. In case of misuse, it is easy for us to withdraw this certificate and block any further access to our Remote Access server. If we receive a Remote Maintenance request, one of our service engineers can initiate a VPN tunnel from his desk (or anywhere in the world, if necessary) to the remote Access server. This way he can lock into the same virtual private network which already “contains“ the customer’s machine and can start the remote maintenance.
The Service engineer is of course required to identify himself with a unique certificate, too.
The Remote Access server has a dynamic address in the internet, this represents another barrier against an attack.
The customer’s miho machine a DNS request (port 53 UDP or TCP) to obtain the address of the miho remote access server (ra1-miho.de, ra1-miho.dyndns.org, ra1-miho.ignorelist.com).
Actually there are also static addresses. but they should not be used, because in case of a change of our internet service provider or access these addresses will be not valid anymore!
After that, the encrypted communication will be initiated by contacting the remote access server on port 5850 (UDP). A socket connection is established using a dynamically assigned port on the client side (as usual with socket connections). Please note that no proxy server is allowed between the customers miho systems and the Internet.
After that, the completely encrypted communication will be done via port 5850 (UDP). Please note that no proxy server is allowed between the customers miho systems and the Internet.
Based on the fact, that the connection request is initiated on the customers side, no port forwarding within the customers firewall is necessary in case of simple network structures (the customer has a specific DSL line for the miho machine (David2; MC3 or NOP2 or Awes PC) only in the DSL router and the machine).
Sample configuration:
Technical requirements
Solution 1 – Standalone:
Separate internet (for example: DSL) connection for miho devices.
Solution 2 – Integration to existing IT system:
Separate network with internet connection through ports 53 (TCP&UDP) & 5850 (UDP) outgoing connection for vpn socket establishment (client: dynamic port). Per miho device is one ip address plus one reserve ip address for service proposes in this network necessary.
For upgrade activities, port 5851 (UDP) outgoing (client: dynamic port) is used.
Alternative: TeamViewer:
In case, that a customer owns a TeamViewer-Licence, we can use it as an alternative way for remote assistance. However, we have to point out that our own solution based on OpenVPN represents the most common among our customers and therefore the best supported solution and that in case of using TeamViewer data traffic may be routed via TeamViewer’s servers for whose security we cannot accept any liability (proprietary software).
Administrator-level access for the customer
The administrator- level access to miho machines and PCs is normally not available for the customer to avoid false configuration and related systems breakdown and loss of production.
In addition this ensures that no viruses or other malware can reach the miho systems or even the customer’s network by installing foreign software.
If the customer explicitly requires the release of the administrator password or their own Administrator account for miho machines and PCs, this can be done by signing this declaration and the reversal of the burden of proof connected with it.
In this case, the burden of proof to name the party causing any damage, e.g.:
- Loss of data
- Loss of production
- Spreading of viruses and other malware
- Software incompatibilities
lies not with miho but the customer.
We understand the above statements and hereby declare that the surrender of administrator access/creation of a customer administrator account for miho devices and PCs is desired at our own request and with the express acceptance of the aforementioned reversal of the burden of proof
(Place, date)
(Legally binding signature and company stamp)
Remote Control
For security reasons, remote maintenance of the machines and devices manufactured by miho is ideally only realised via a direct connection via an independent Internet access (customer provides suitable Internet access).
With this architecture, any connection to the customer’s network is avoided.
This ensures that neither viruses or other malware from miho devices can interfere with the customer’s network, nor conversely, that the above-mentioned software can influence miho devices.
If the customer explicitly demands a connection of miho equipment to an existing network such connection can be established.
In this case, however, miho cannot accept any responsibility for damages that are directly or indirectly caused by that network connection and which are not caused by miho, e.g. explicitly:
- Loss of data
- Loss of production
Due to spreading of viruses or other damaging software, or plain software incompatibilities.
In this case, the burden of proof lies with the customer.
We understand the above statements and hereby declare that the networking of miho devices is desired at our own request and with express acceptance of the aforementioned risks.
(Place, date)
(Legally binding signature and company stamp)
Production data aquisition
The transfer of production data of the machines made by miho is preferably done via the following means, due to security reasons:
- Direct connection of a production data collection system (PC) via an individual network connection
This way, any connection to the customers network will be avoided.
This ensures, that neither viruses or other malware from miho machines can disturb the customer’s network nor that on the other way, such software can obtain influence on miho machines.
If the customer explicitly demands a connection of miho equipment to their company network this can be technically implemented/supported.
The prerequisite is that the customer guarantees a minimum bandwidth of 256 Kbps for the socket connection of the BDE on the route between the miho device and the BDE (port 50,000 TCP).
The query duration over a viewer that may have been connected over a WAN depends heavily on the available bandwidth. It requires a bandwidth of at least 4 Mbps and a bandwidth of 10 Mbps is strongly recommended!
In this case, however, miho cannot accept any responsibility for damages that are directly or indirectly caused by that network connection and which are not caused by miho, e.g. explicitly:
- Loss of data
- Loss of production
Due to spreading of viruses or other damaging software, or plain software incompatibilities.
miho guarantees that the delivered machines and devices are free of viruses and other malware at the time of delivery. As the devices are accessible to maintenance personnel etc., the burden of proof lies with the customer in the event of damage.
We understand the above statements and hereby declare that the networking of miho devices is desired at our own request and with express acceptance of the aforementioned risks.
(Place, date)
(Legally binding signature and company stamp)
Preconditions for installation and maintenance
Both for the installation of the various software components for remote maintenance, as well as the production data acquisition, we need local administrator accounts.
The customer must ensure, especially if our systems shall be integrated into the customer’s network that on the agreed installation time an employee of his IT department is available for the smooth handling of the necessary integration work.
